Section outline
-
-
Example candidate response
-
All information and advice in this section is specific to the example question and response being demonstrated. It should give you an idea of how your responses might be viewed by an examiner but it is not a list of what to do in all questions. In your own examination, you will need to pay careful attention to what each question is asking you to do.
-
Question
The question used in this example is from Paper 3 and and requires knowledge and understanding of the TCP/IP stack, together with knowledge of protocols and understanding of what they are used for and how they are used.2) The TCP/IP protocol suite can be viewed as a stack with four layers.(a) Complete the stack by inserting the names of the three missing layers.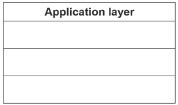 Complete is the command word in this question. This means that you add information to an incomplete diagram.b) BitTorrent is a protocol used at the Application layer for an exchange of data.i) State the network model used with this protocol.State is the command word in this question. This means that you should write the answer clearly and succinctly, you may only need to use a few words.ii) State the use of BitTorrent.iii) Explain how applications use BitTorrent to exchange data.Explain how are the command words in this question. This means that you should set out the method used to perform the given task showing that you understand how the method used is applied to the situation set out in the question..(c) State two other protocols that are used at the Application layer for the exchange of data.For each protocol, give a different example of an appropriate exchange of data.Give is the command word in this question. This means that you should recall from your own knowledge.
Complete is the command word in this question. This means that you add information to an incomplete diagram.b) BitTorrent is a protocol used at the Application layer for an exchange of data.i) State the network model used with this protocol.State is the command word in this question. This means that you should write the answer clearly and succinctly, you may only need to use a few words.ii) State the use of BitTorrent.iii) Explain how applications use BitTorrent to exchange data.Explain how are the command words in this question. This means that you should set out the method used to perform the given task showing that you understand how the method used is applied to the situation set out in the question..(c) State two other protocols that are used at the Application layer for the exchange of data.For each protocol, give a different example of an appropriate exchange of data.Give is the command word in this question. This means that you should recall from your own knowledge. -
-
Please rotate your device
-
Example candidate response and examiner comments
-
(a)
Application layer
Transport (layer)
Internet (layer)
Network (access layer)
[See examiner comment]
(b)
(i) Peer – to – peer.
(ii) File sharing.
(iii) BitTorrent client software is made available, this is used to load the torrent descriptor for the required file by computers joining it swarm. A server, called tracker, keeps records of all the computers joining the swarm and allows them to connect to each other by sharing their IP addresses.
The torrent is split into small pieces that can be downloaded or uploaded by each computer in the swarm. Once a computer has downloaded a piece of the torrent file it can upload that piece to other computers in the swarm and become a seed.
(c)
Protocol 1 SMTP
Example Sending email messages
Protocol POP3
Example retirement of email messages
[See examiner comment]
[Total mark awarded] -
-
